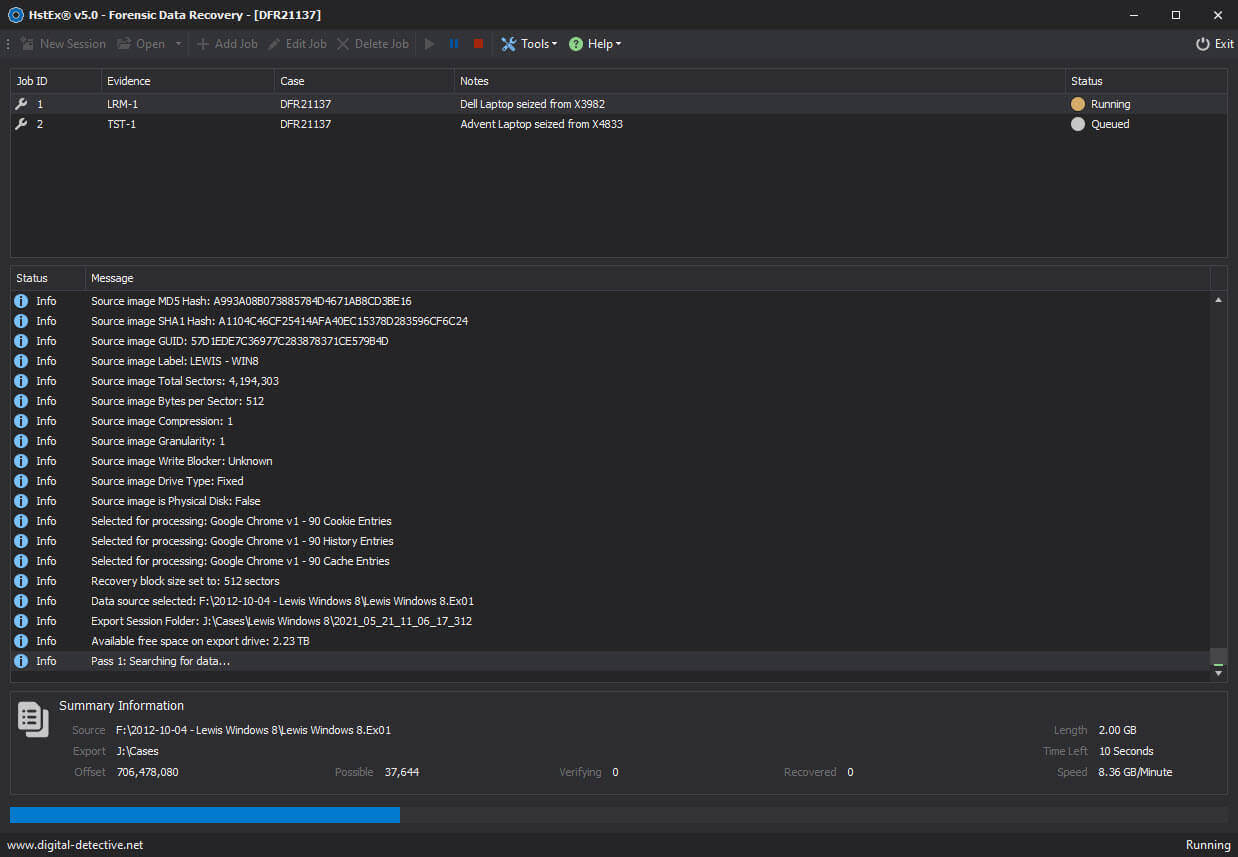
Recover Deleted Web Browser Data
HstEx® is a fundamental and indispensable application which is included as part of the NetAnalysis® suite. It is an advanced data recovery tool and is designed to recover deleted web browser artefacts from a wide-variety of forensic sources such as evidence files (e01, ex01, dd, etc.) and dump files from mobile extraction tools.
Whilst NetAnalysis® works at the file system level and imports from live files, HstEx® works at the sector level and uses our intelligent carving technology called Intelli-Carve®. Intelli-Carve® moves far beyond simple carving techniques and utilises cutting-edge technology to recover and verify the integrity of the data. For example, HstEx® can recover deleted SQlite records, ESE database entries, browser cache entries, binary Plists and many other relevant file formats.
HstEx® recovers the data and writes it into a proprietary output file which can then be easily imported into NetAnalysis® for examination and analysis.
Forensic Software
Digital Detective develops innovative digital forensic software products designed to deliver cutting edge features for the preservation, extraction, analysis and presentation of evidence from computer and other digital devices.
Browser Forensic Analysis
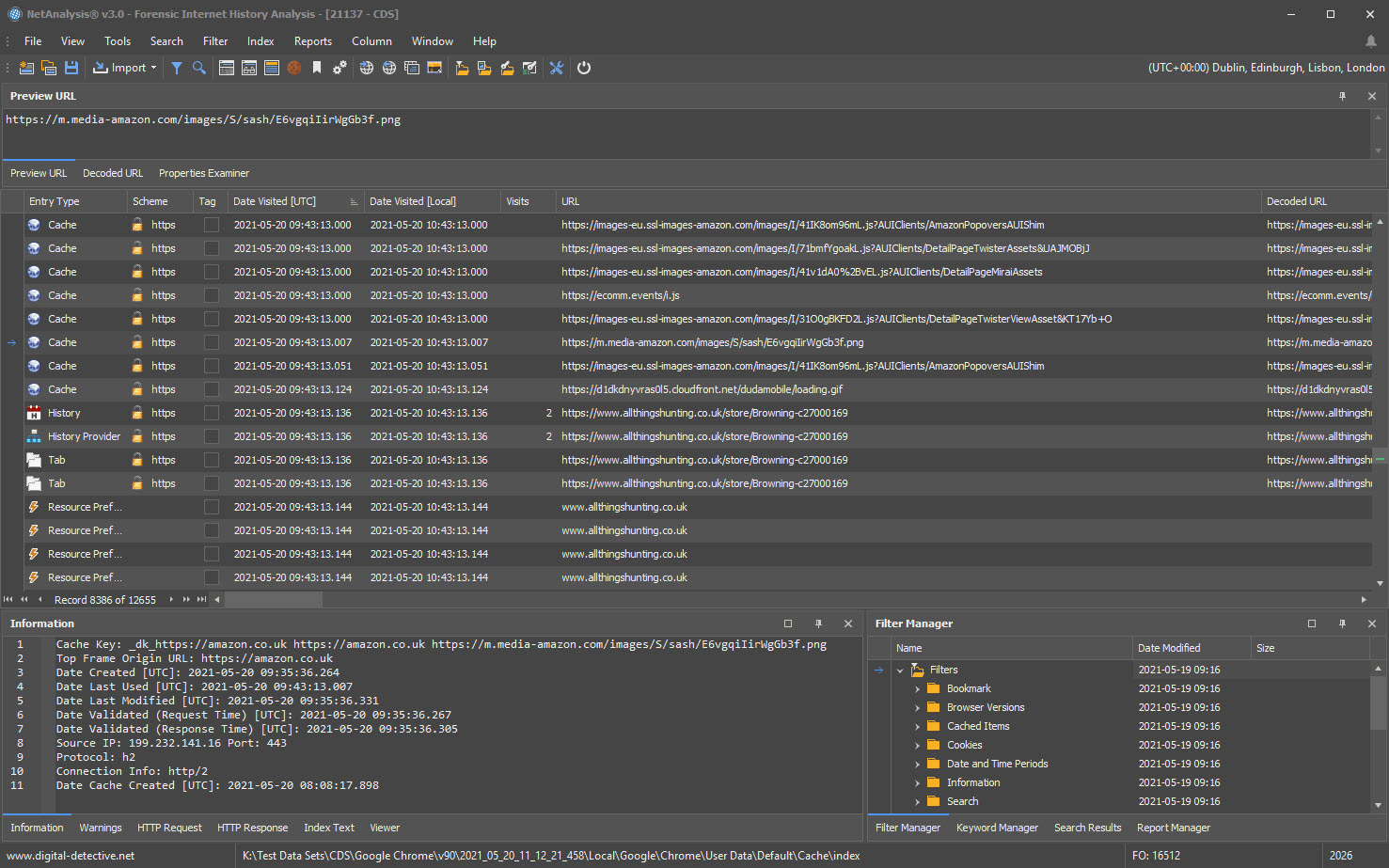
Digital Detective’s NetAnalysis® is our flagship product and is the industry leading forensic software for the extraction and analysis of Internet browser trace evidence. It is trusted by the leading worldwide Law Enforcement agencies.
Advanced Carving
Digital Detective’s Blade® Professional is an extremely fast and accurate data carving recovery solution. Utilising our Intelli-Carve® technology, it is highly effective in recovering data from hard disks and mobile phone dumps.