Userdata History Type in Internet Explorer
Introduction to Userdata
Internet Explorer 8+ user data persistence is a function which allows online forms to save a small file to the system with information about values entered in a particular form. This allows the user to retrieve a half filled web based form when they revisit.
Persistence creates new opportunities for website authors. Information that persists beyond a single page without support from the server, or within the finite scope of cookies, can increase the speed of navigation and content authoring.
The folder structure where the data is actually stored is very much like the standard Internet Explorer cache folder structure. Inside the cache folder you will find the files containing data attributed to the associated website.
{user}\AppData\Roaming\Microsoft\Internet Explorer\UserData\
To demonstrate how this works, we have created a page which allows you to save a string to the local drive.
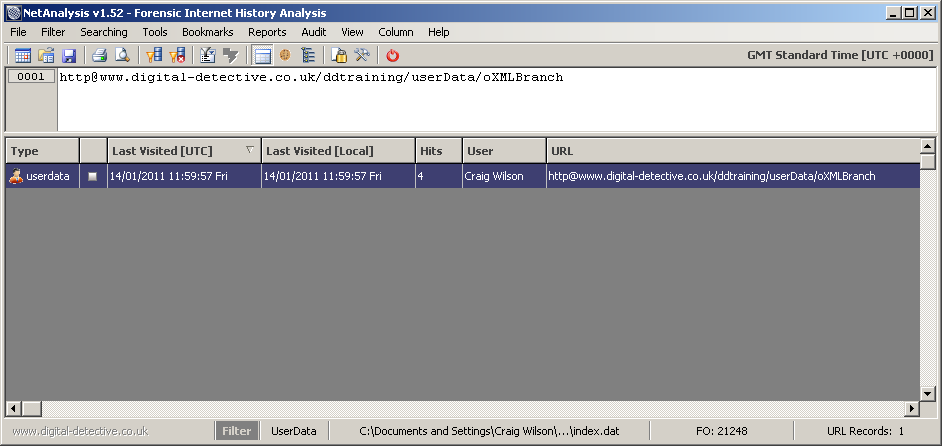
Once you have saved some string data using the above page, open the UserData INDEX.DAT file in NetAnalysis and review the entries. Selecting F8 will bring up the search/filter dialogue. Change the field name to ‘Type’ and enter ‘userdata’ in the filter text box. When this is executed, you should find an entry as shown below:
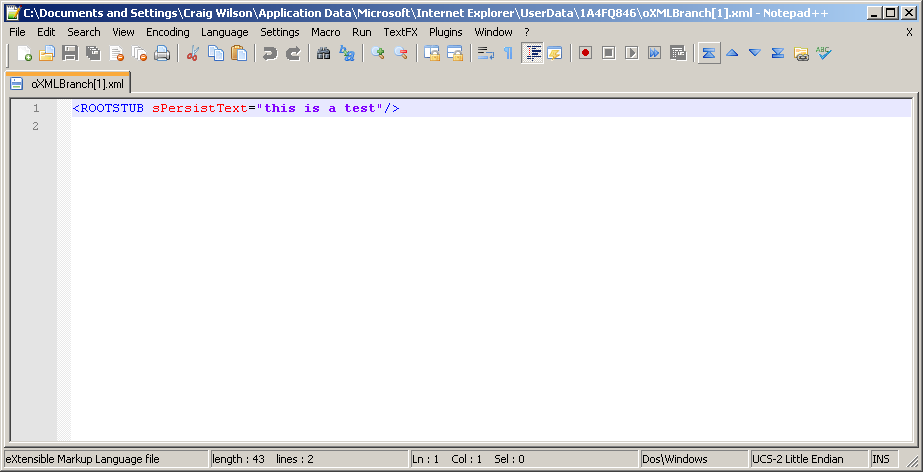
If you navigate to the corresponding folder, you will find an XML file which contains the string you entered into the website. This is shown below.










Great artifact – thank you for your continued research.