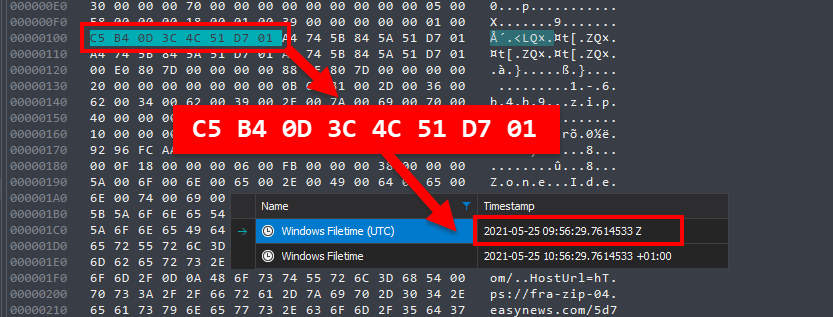
Decoding the Mysteries of Time with DCode™ v5.6 In the intricate tapestry of digital forensics, where every digital footprint tells a story, timestamps serve as the silent guardians of truth. Welcome to DCode™ – The Digital Detective’s Companion Across Time, where we embark on a journey to decode the mysteries of time with precision and […]
Why is this Important? During a forensic examination, establishing a timeline of events is usually an important aspect in the analytical process. This may involve you having to identify when a hard disk was manufactured. If you are a data recovery engineer, this information can also be useful when trying to identify donor drives and […]
Zone Identifier, ADS and URL Zones If you are new to the field of digital forensics, you may not be aware of Zone Identifiers, Alternate Data Streams (ADS) or URL Zones. If that is the case, then you have come to the right place. We shall explain all and show you exactly how they can […]
There are two different methods for describing the order in which a sequence of bytes are stored in digital systems: Big Endian: places the most significant byte first (also known as network byte order) Little Endian: places the least significant byte first Etymology The term endian comes from the novel Gulliver’s Travels by Jonathan Swift. […]
Understanding Number Systems Number systems use different number bases. A number base indicates how many different digits are available when using a particular numbering system. For example, decimal is number base 10, which means it uses ten digits: 0, 1, 2, 3, 4, 5, 6, 7, 8 and 9. Binary is number base 2, which […]
Introduction to Character Encoding Understanding how Character Encoding works is an essential part of understanding digital evidence. It is part of the common core of skills and knowledge. A character set is a collection of letters and symbols used in a writing system. For example, the ASCII character set covers letters and symbols for English […]
Introduction When using third party image mounting tools to perform the forensic examination of NTFS file systems, it is extremely important to understand NTFS Junction Points so that you don’t find yourself making a critical mistake during your analysis. An issue has been identified with third party image mounting software where NTFS junction points are […]
Introduction to Blade® v1.9 We are pleased to announce the release of Blade v1.9. This release of Blade® brings a number of fixes and some great new features. This is the first release of Blade® to have evaluation capabilities which allow the user to test and evaluate our software for 30 days. When Blade™ is installed […]
Internet Explorer Data As forensic examiners will be aware, Microsoft Internet Explorer stores cached data within randomly assigned folders. This behaviour was designed to prevent Internet data being stored in predictable locations on the local system in order to foil a number of attack types. Prior to the release of Internet Explorer v9.0.2, cookies were […]
Introduction to Userdata Internet Explorer 8+ user data persistence is a function which allows online forms to save a small file to the system with information about values entered in a particular form. This allows the user to retrieve a half filled web based form when they revisit. Persistence creates new opportunities for website authors. Information […]
About US
Digital Detective enhances digital forensic science though cutting edge research and development.
We offer a range of products and services for digital forensic analysis and advanced data recovery.
Product tags
Select Language
Translate our site by selecting your language from the option below.
Contact Us
Digital Detective Group
Motis Business Centre
Cheriton High Street
Folkestone
KENT, CT19 4QJ
United Kingdom
///courts.endearing.bulbs
+44 (0) 20 3384 3587

 Digital Detective©
Digital Detective©